In the world of cryptography, the Blowfish algorithm is a symmetric key block cipher known for its speed and strong security. Created by Bruce Schneier in 1993, Blowfish quickly gained popularity as a reliable encryption technique.
Its robustness, flexibility, and ease of implementation make it a valuable tool for protecting sensitive information. This article will delve into the workings of the Blowfish algorithm, exploring its key features, encryption process, and practical applications.
Quick Summary
- The Blowfish algorithm is a symmetric key block cipher known for its speed, flexibility, and robust security features.
- It operates with variable key sizes ranging from 32 to 448 bits and a fixed block size of 64 bits.
- The algorithm generates subkeys through a key expansion process and employs a Feistel network structure for encryption rounds.
- Blowfish is found in many practical applications like secure file storage, VPNs, password protection, secure communication protocols, and online banking.
- While Blowfish remains a viable option, AES is now generally considered more secure and widely adopted.
What is The Blowfish Algorithm?
The Blowfish algorithm is a symmetric key block cipher. It uses the same key for encryption and decryption, with the primary goal being data security. It secures data by transforming it into an unreadable form, known as ciphertext, which can only be converted back to its original state using the same key.
To truly understand the Blowfish algorithm, let's break it down into its core components and explain how it operates. As you delve into the inner workings of this encryption technique, you'll gain a comprehensive understanding of its design and functionality.
Also Read; What is AES Encryption and How Does It Work?
How The Blowfish Algorithm Works
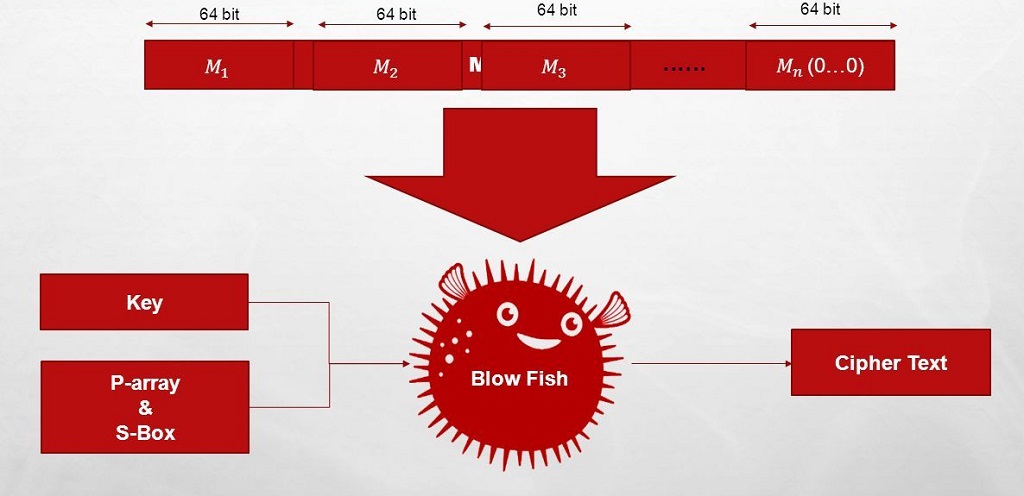
To truly grasp the concept of the Blowfish algorithm, it is essential to understand symmetric key block ciphers. In symmetric key encryption, the same key is used for both the encryption and decryption processes.
Plaintext, or the original data, is divided into fixed-size blocks before undergoing encryption. Each block is encrypted using the same key, resulting in a corresponding ciphertext block.
Block ciphers are a specific type of symmetric key encryption where the plaintext is divided into fixed-size blocks, typically 64 or 128 bits. These blocks are then individually encrypted using the key. Block ciphers provide an efficient way to encrypt large amounts of data by breaking it into manageable chunks.
Symmetric key block ciphers offer several advantages, such as speed and simplicity. The process can be performed quickly since the same key is used for encryption and decryption. Additionally, the simplicity of symmetric key block ciphers makes them suitable for resource-constrained devices and applications.
However, symmetric key block ciphers also have some drawbacks. One of the main challenges is securely exchanging the key between the sender and recipient. The key must be kept confidential to prevent unauthorized access to the encrypted data. Additionally, if the same key is compromised, all the encrypted data is at risk.
Key Features of the Blowfish Algorithm

The Blowfish algorithm possesses several key features that distinguish it from other encryption techniques.
Key Size and Block Size Flexibility
Firstly, Blowfish allows for flexible key sizes, ranging from 32 to 448 bits. This adaptability enables users to choose the level of security based on their specific requirements. Additionally, Blowfish has a fixed block size of 64 bits, meaning each plaintext block is encrypted separately.
Subkey Generation Using the Key Expansion Function
Subkey generation is a critical aspect of the Blowfish algorithm. During the key expansion phase, the key expansion function transforms the original key into a series of subkeys.
These subkeys play a vital role in the encryption process, ensuring the security and integrity of the data. The Blowfish algorithm employs a complex key schedule algorithm to generate these subkeys efficiently.
Use of The Feistel Network Structure
The Feistel network structure is another notable feature of Blowfish. This structure divides the plaintext into two halves and applies a series of rounds to each. Substitution and permutation operations are performed at each round using the generated subkeys.
The Feistel network structure ensures the diffusion and confusion of the data, enhancing the algorithm's security.
Pros and Cons of Using The Blowfish Algorithm
Although newer algorithms have come into focus, Blowfish remains a valuable tool for protecting sensitive information and ensuring secure network communication. The key to employing it correctly lies in understanding when its advantages (and weaknesses) lie.
Advantages
- Blowfish is highly efficient and fast, making it suitable for resource-constrained devices and applications.
- The variable key size allows users to adjust the level of security based on their requirements.
- Blowfish has withstood extensive cryptanalysis and has no known practical vulnerabilities.
- It is an open-source algorithm, enabling peer review and fostering trust within the cryptography community.
Disadvantage
- Blowfish has been primarily replaced by more advanced algorithms, such as Advanced Encryption Standard (AES), which offer improved security features.
- The block size of 64 bits may be susceptible to specific cryptographic attacks, especially when dealing with large amounts of data.
- The key schedule algorithm can be computationally expensive, particularly for large key sizes.
Also Read; Understanding How Data Encryption Safeguards Your Information
Examples of Blowfish Algorithm Applications
The practical applications of the Blowfish algorithm are vast and diverse. Blowfish has proven effective across multiple domains, from securing sensitive data in storage systems and Virtual Private Networks (VPNs) to password protection and secure electronic transactions.
Here are some examples of how Blowfish is still in use today;
Secure File Storage
One practical application of the Blowfish algorithm is secure file storage. Many organizations and individuals rely on Blowfish encryption to protect sensitive files stored on local drives or cloud storage platforms.
By encrypting files with Blowfish, users can ensure that even if unauthorized individuals gain access to the storage medium, they won't be able to decipher the contents without the encryption key.
Examples;
AxCrypt: AxCrypt is a file encryption software that allows users to secure their files and folders with strong encryption. It offers Blowfish as one of the encryption algorithms to protect sensitive data stored on local drives or in cloud storage.
Boxcryptor: Boxcryptor is a cloud encryption service that enables users to encrypt their files before uploading them to cloud storage providers like Dropbox, Google Drive, or OneDrive. It supports Blowfish encryption as one of the encryption options to ensure data privacy and security.
SecureZIP: SecureZIP is a compression and encryption software that offers secure file storage capabilities. It utilizes Blowfish encryption to protect files and folders, allowing users to store and share sensitive data while maintaining data integrity securely.
Virtual Private Networks
Blowfish is often used in VPN protocols to secure data transmissions between users and remote networks. VPNs establish encrypted tunnels that shield sensitive information from potential eavesdroppers and hackers.
Blowfish's speed and efficiency make it a popular choice for encrypting VPN connections, ensuring the confidentiality and integrity of the data exchanged between the user's device and the remote network.
Examples;
SoftEther VPN: SoftEther VPN is an open-source VPN software that supports various encryption algorithms, including Blowfish. It allows users to establish secure VPN connections using Blowfish encryption, ensuring the confidentiality and integrity of their network communications.
Zyxel VPN Clients: Zyxel VPN clients, used in Zyxel network devices, offer support for Blowfish encryption. These clients enable users to connect to VPNs using Blowfish encryption, providing secure access to remote networks and protecting sensitive data during transmission.
TheGreenBow VPN Client: TheGreenBow VPN Client is a widely used VPN software that supports various encryption algorithms, including Blowfish. It allows users to establish secure VPN connections using Blowfish encryption, ensuring the privacy and security of their network traffic.
Password Protection
Blowfish plays a vital role in password protection mechanisms. Users who create accounts on websites or online services often store their passwords as hashed representations rather than plaintext.
Blowfish-based password hashing algorithms transform passwords into irreversible hashes using the Blowfish algorithm. This ensures that even if the stored data is compromised, the original passwords cannot be quickly recovered, enhancing the security of user accounts.
Examples;
bcrypt: bcrypt is a password hashing algorithm that uses Blowfish as its underlying encryption algorithm. It is widely used in software applications and systems to securely store and authenticate passwords, providing additional protection against password-related attacks.
KeePass: KeePass is a popular open-source password manager that uses Blowfish encryption to protect stored passwords and other sensitive information. It offers robust password protection and ensures the user's login credentials remain secure.
Password Depot: Password Depot is a password management software with Blowfish encryption to safeguard users' passwords and sensitive data. It provides a secure and centralized storage solution for managing and protecting passwords across multiple platforms.
Secure Communication Protocols
Blowfish is employed in various secure communication protocols to safeguard sensitive information during transmission. For example, Blowfish can be used in email encryption systems to encrypt the contents of emails, preventing unauthorized access to the message content.
Additionally, Blowfish can be integrated into secure messaging applications, ensuring that text messages, voice calls, and multimedia files exchanged between users remain private and protected.
Examples;
OpenVPN: OpenVPN, a widely used open-source VPN protocol, allows users to establish secure and encrypted connections. It supports Blowfish encryption as one of the available encryption algorithms for securing network communications.
SSL/TLS: Although AES is more commonly used in SSL/TLS protocols, some legacy systems or less common configurations may still employ Blowfish as an option for encryption during secure communications.
ZRTP: ZRTP is a secure communication protocol for voice and video calls. While it primarily utilizes other encryption algorithms like AES, Blowfish can be an alternative encryption option in some ZRTP implementations.
Online Banking and eCommerce
Blowfish finds significant use in securing online banking transactions and eCommerce platforms. When users make online payments or perform financial transactions, Blowfish encryption is often employed to protect sensitive data, such as credit card details and personal information.
By encrypting this information with Blowfish, financial institutions and online merchants can ensure that it remains confidential and cannot be intercepted or tampered with by malicious actors.
Examples;
Zen Cart: Zen Cart is an open-source eCommerce platform that offers Blowfish encryption as one of the encryption options for securing customer data during online transactions. It provides a customizable online store solution and includes Blowfish as a legacy encryption choice.
X-Cart: X-Cart is a popular eCommerce platform that offers Blowfish encryption as one of its encryption options. It provides a range of features for creating and managing online stores while prioritizing the security of customer data during online transactions.
PrestaShop: PrestaShop is a popular eCommerce software offering various features for creating online stores. While PrestaShop primarily utilizes more robust encryption algorithms like AES, Blowfish encryption can still be supported through specific plugins or extensions.
Also Read; The Complete VPN Guide for Beginners
Comparing Blowfish vs. AES
Blowfish and Advanced Encryption Standard (AES) are both widely used symmetric key block ciphers, but they have critical differences in security, performance, and adoption. Generally, however, AES is considered more secure and efficient than Blowfish.
While Blowfish remains a viable option for specific applications, AES has become the preferred choice for new cryptographic implementations.
When choosing between Blowfish and AES, it is recommended to consider the specific security requirements, performance considerations, and the availability of cryptographic support in the target environment.
Security
AES is considered more secure than Blowfish. AES has undergone extensive scrutiny and analysis by the cryptographic community and has been selected as the standard encryption algorithm by the U.S. government.
It has a fixed block size of 128 bits and supports key sizes of 128, 192, and 256 bits, providing high security. Blowfish, however, supports variable key sizes ranging from 32 to 448 bits but has a fixed block size of 64 bits. While Blowfish is still considered secure, AES is generally recommended for new applications due to its more robust cryptographic properties.
Performance
AES generally outperforms Blowfish in terms of speed and efficiency. AES has been optimized for modern computer architectures, and hardware implementations of AES are widely available, making it faster in both software and hardware implementations.
Blowfish, while still relatively fast, can be slower than AES, especially when dealing with large amounts of data. This performance advantage has contributed to the widespread adoption of AES in various applications.
Adoption
AES has gained widespread adoption and is considered the de facto standard for symmetric key encryption. Many security protocols and applications, including VPNs, secure messaging apps, and file encryption tools, use AES as their preferred encryption algorithm.
Blowfish, although widespread in the past, has declined its usage and adoption due to the emergence of AES and its more robust security properties.
Final Thoughts: The Legacy and Future of the Blowfish Algorithm
The Blowfish algorithm has played a significant role in the world of cryptography since its inception. Its speed, flexibility, and robust security features have made it a popular choice for securing sensitive data in various applications.
While the Blowfish algorithm remains viable for specific use cases, we must acknowledge that newer encryption algorithms, such as AES, have emerged as more secure and widely adopted alternatives.
As technology evolves, the lessons learned from Blowfish will shape future encryption techniques, ensuring the ongoing protection of sensitive information in the digital world.